"Security company Trellix warns of a sharp increase in advanced phishing attacks on Facebook users. In the second half of 2025, researchers saw a rise in the use of the 'Browser-in-the-Browser' technique, in which attackers simulate fake login windows that are almost indistinguishable from the real thing. With more than 3 billion active users, Facebook remains an attractive target for cybercriminals. In recent months, however, the approach has been evolving rapidly."
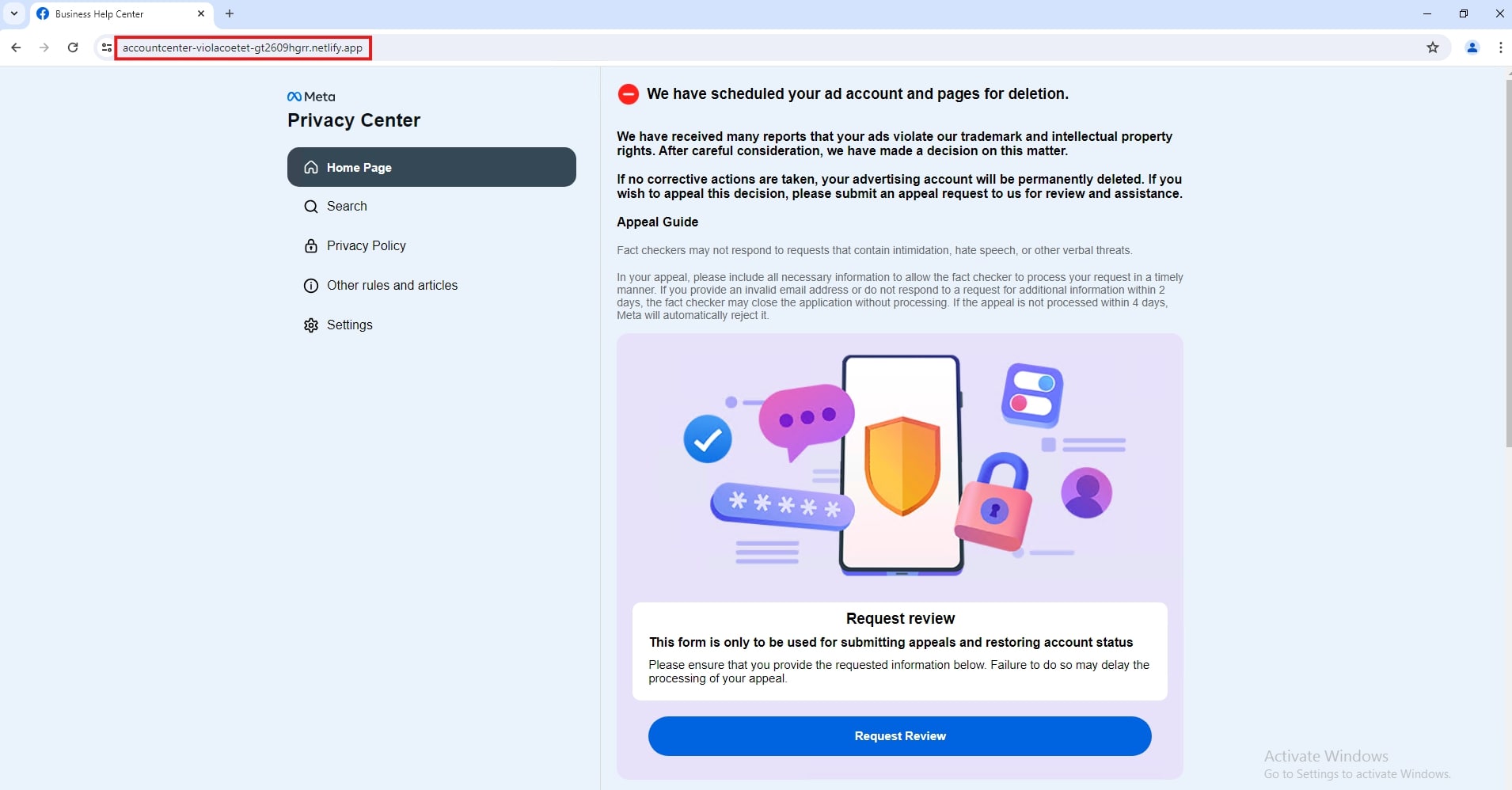
"The Browser-in-the-Browser (BitB) technique displays a fully simulated Facebook login window within the user's browser. The fake window even contains the real Facebook URL in the address bar, making it virtually impossible to visually distinguish it is from legitimate login page. Criminals build these interfaces entirely from scratch, including hardcoded URLs designed to inspire trust. In addition to the BitB method, researchers are also seeing an increase in the abuse of legitimate cloud platforms."
Phishing targeting Facebook has shifted from simple fake links to more technically complex methods, notably the Browser-in-the-Browser (BitB) technique that simulates login windows inside browsers. BitB displays a fully simulated Facebook login with the real URL visible in the address bar and uses hardcoded URLs to build trust. Attackers increasingly host fake pages on trusted cloud platforms such as Netlify and Vercel to bypass security filters. Typical campaigns use emails with shortened URLs redirecting to fake Meta captcha pages and present Facebook login prompts to steal credentials. Common lures include copyright claims, suspicious logins, and urgent verification requests. Two-factor authentication remains the primary defense.
Read at Techzine Global
Unable to calculate read time
Collection
[
|
...
]