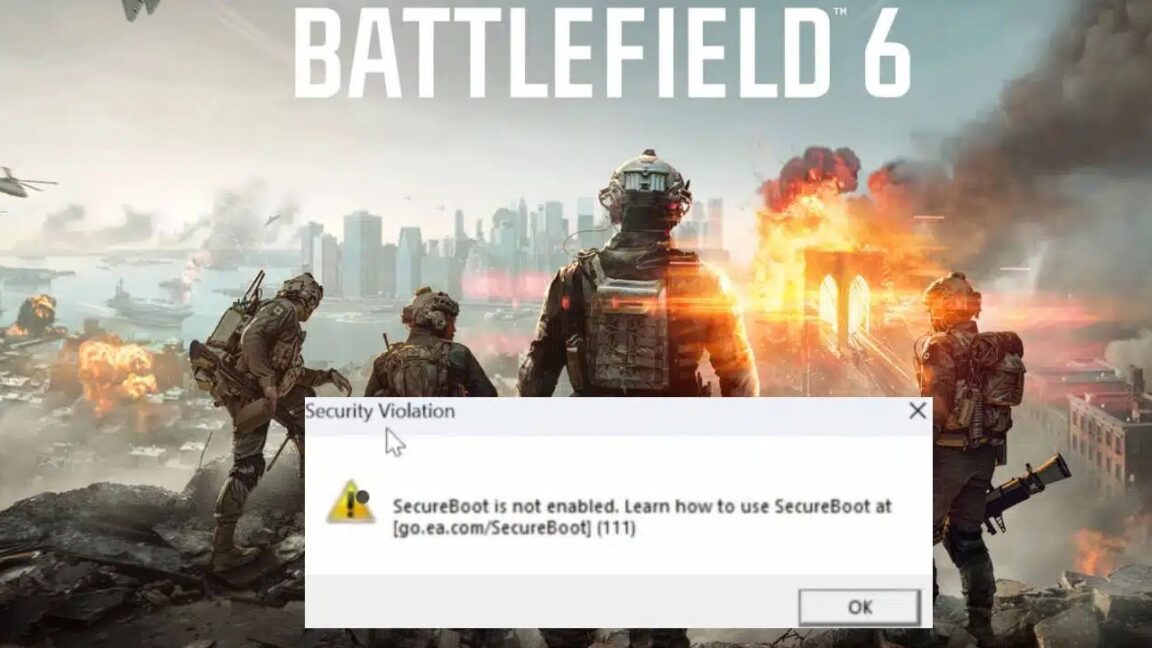
"When announcing the Secure Boot requirement in a Steam forum post prior to the open beta, EA explained that having Secure Boot enabled "provides us with features that we can leverage against cheats that attempt to infiltrate during the Windows boot process." Having access to the Trusted Platform Module on the motherboard via Secure Boot provides the anti-cheat team with visibility into things like kernel-level cheats and rootkits, memory manipulation, injection spoofing, hardware ID"
""The fact is I wish we didn't have to do things like Secure Boot," Buhl said in an interview with Eurogamer. "It does prevent some players from playing the game. Some people's PCs can't handle it and they can't play: that really sucks. I wish everyone could play the game with low friction and not have to do these sorts of things.""
Battlefield 6's PC open beta requires Secure Boot enabled in Windows and BIOS to grant anti-cheat tools low-level system access. Secure Boot combined with TPM access provides visibility into kernel-level cheats, rootkits, memory manipulation, injection spoofing, and hardware ID techniques. The requirement prevents some players from playing due to incompatible PCs and deters others unwilling to allow kernel-level anti-cheat access. Secure Boot does not make cheating impossible but substantially increases the difficulty of cheating and makes detection and removal easier. The choice generates controversy because of technical fragility and privacy and security concerns over kernel-level access.
Read at Ars Technica
Unable to calculate read time
Collection
[
|
...
]