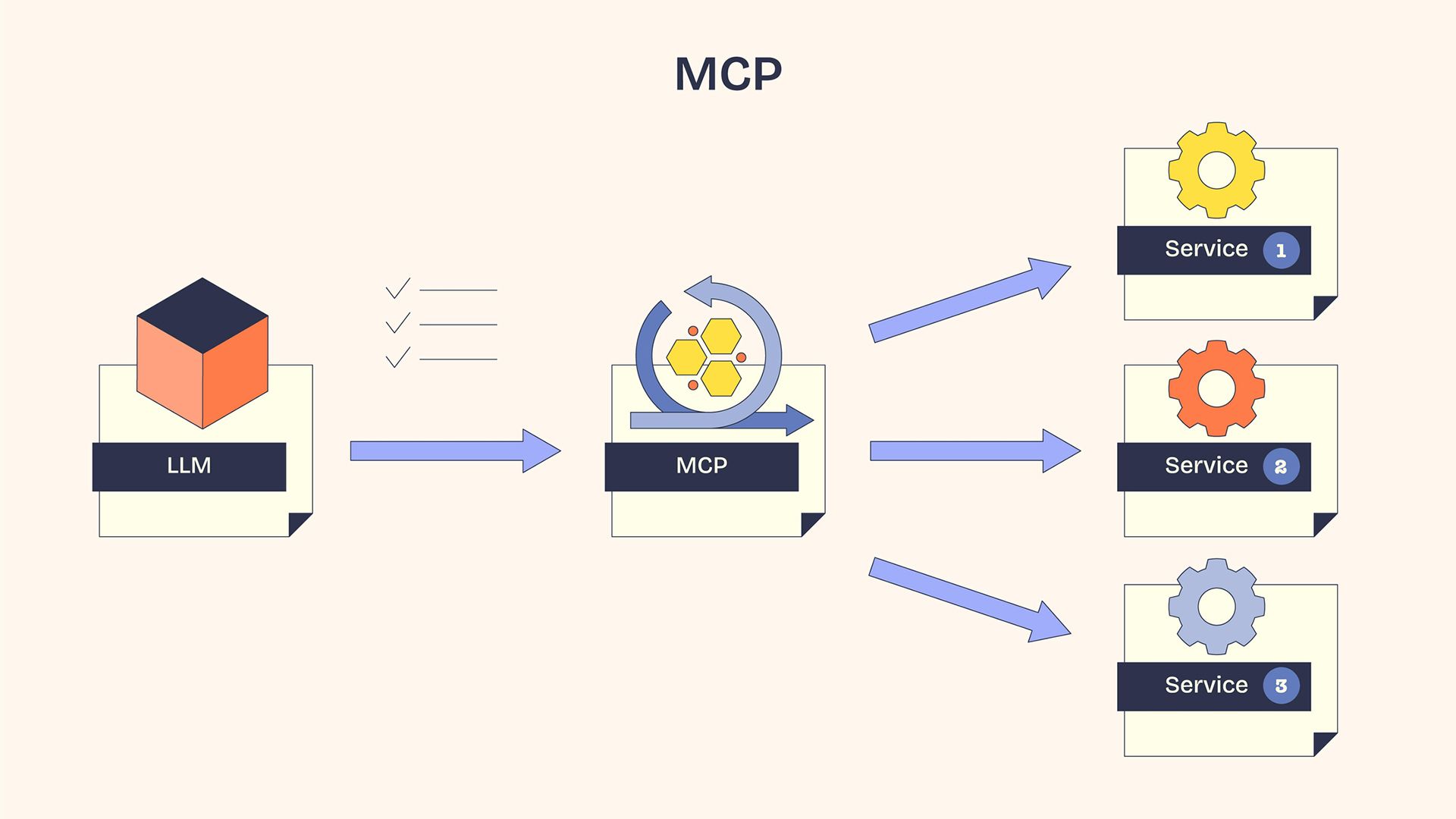
#mcp
#mcp
[ follow ]
#ai #ai-agents #ai-integration #anthropic #open-source #ai-security #model-context-protocol #agentic-ai
fromGitHub
1 day agoGitHub - Techthos/clockwork: Clockwork-MCP is a local executable MCP-Server that gives Agents the ability to simple track project worklogs.
Clockwork is a Model Context Protocol (MCP) server that automatically tracks your work time based on git commits. It aggregates commits into worklog entries, calculates durations, and manages projects - all through a simple CLI interface. Automatic Commit Aggregation: Automatically collects commits since your last worklog entry Smart Duration Calculation: Estimates work time based on commit timestamps Project Management: Track multiple projects with associated git repositories
Software development
fromInfoWorld
2 days agoDescope introduces Agentic Identity Hub 2.0 for managing AI agents
Descope has announced Agentic Identity Hub 2.0, an update to its no-code identity platform for AI agents and Model Context Protocol (MCP) servers. The new release gives developers and security teams a dedicated UI and control plane to manage authorization, access control, credentials, and policies for AI agents and MCP servers, Descope said. Unveiled January 26, Agentic Identity Hub 2.0 lets MCP developers and AI agent builders use the platform to manage AI agents as first-class identities alongside human users,
Information security
fromTheregister
1 month agoSalesforce adds ChatGPT to rein in DIY data leaks
Keenan wrote that Salesforce users have been building their own MCP servers using OpenAI's Apps SDK and exposing Salesforce data to various frontier LLMs in the bargain. That puts the company's data outside the governance and usage metering of Salesforce. "The thing that I worry about, and what I wanted to get ahead of, was homegrown MCP servers from customers just spitting out data to OpenAI around the trust boundary," Billmaier told Keenan. "And with this, we're actually kind of being full of our destiny as we think about other players emerging in this space."
Artificial intelligence
fromTechzine Global
1 month agoNetskope launches security for Model Context Protocol
Netskope introduces security capabilities for Model Context Protocol (MCP) communication. The functionality is designed to help organizations deploy AI agents securely. MCP communication enables AI systems to connect to business data and issue autonomous commands. MCP was launched by Anthropic in November 2024 as an open standard for connecting AI agents to external systems. The protocol acts as a universal adapter between AI applications and business assets.
Information security
Artificial intelligence
fromTechzine Global
2 months agoModel Context Protocol receives major update on its first anniversary
Anthropic updated the Model Context Protocol with task-based workflows, URL-based client registration, and sampling-with-tools, simplifying authorization and supporting complex long-running operations.
fromGitHub
2 months agoGitHub - mcpland/mock-mcp: Mock MCP Server - AI-driven mock data orchestration with OpenAPI JSON Schema for testing
Install the package. Add mock-mcp as a dev dependency inside your project. npm install -D mock-mcp yarn add -D mock-mcp pnpm add -D mock-mcp Configure the Model Context Protocol server. For example, Claude Desktop can launch the binary through npx: Connect from your tests. Use connect to retrieve a mock client and request data for intercepted calls. Run with MCP enabled. Prompt your AI client to run the persistent test command and provide mocks through the tools.
Software development
fromInfoWorld
3 months agoMicrosoft unveils framework for building agentic AI apps
Agents can dynamically discover and invoke external tools or data servers exposed over MCP. Agents can collaborate across runtimes using structured, A2A protocol-driven messaging. Any REST API with an OpenAPI specification can be imported as a callable tool instantly. Agents can run in containers, on-premises, or across multiple clouds, making them portable across environments. The Agent Framework supports a wide
Artificial intelligence
fromThe Verge
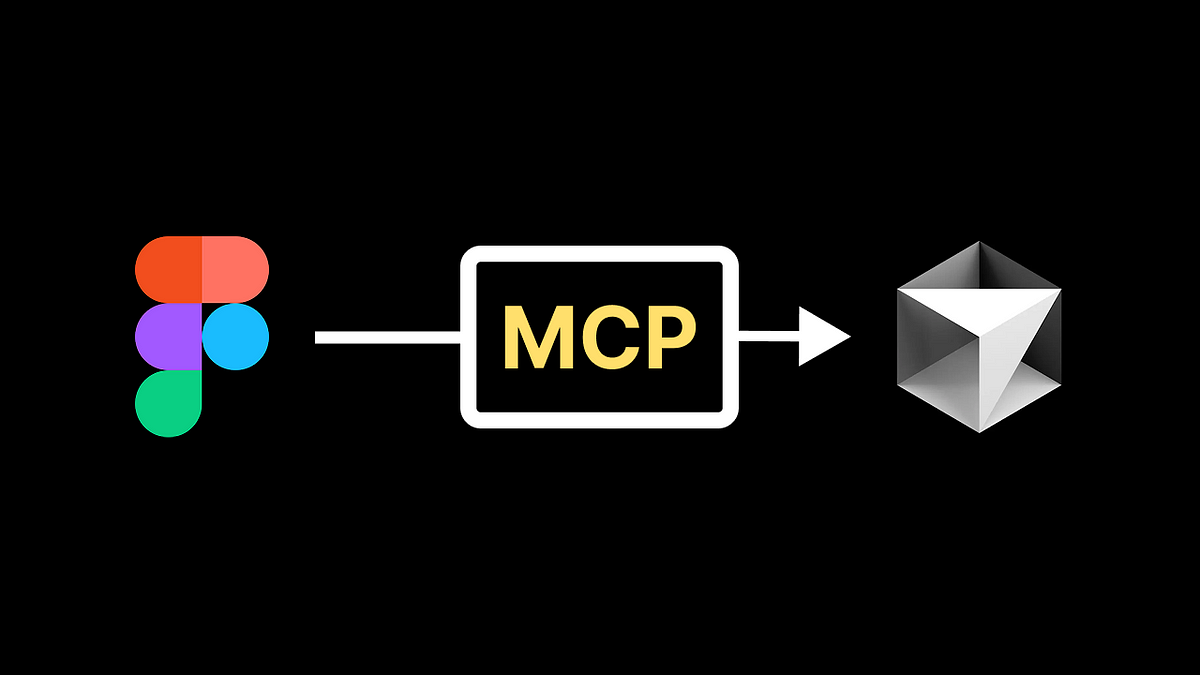
4 months agoFigma made its design tools more accessible to AI agents
Figma is launching some new updates that allow AI models to directly communicate with its app-building tool and access designs remotely. Figma's Model Context Protocol (MCP) server - a bridge that enables AI models to tap directly into the code behind prototypes and designs created using Figma's tools - has now been expanded to support the design platform's AI prompt-to-app coding tool, Figma Make.
UX design
fromTechzine Global
4 months agoPega Smart Investigate gets agentic AI boost for faster detection of payment exceptions
Pega Smart Investigate Agentic Automation promises banks faster and cheaper handling of payment exceptions. These are cases in which payment is not or cannot be made. The updated version primarily adds extra generative AI capabilities to the existing offering. This should lead to better automated handling of cases requiring investigation. Many banks still rely on manual processes to handle cases where payment has not been made. This is despite the growing complexity of the market.
Artificial intelligence
fromInfoQ
4 months agoHoneycomb Hosted MCP Brings Observability Data into the IDE
MCP provides a structured interface for tools and AI agents to query observability data, enabling developers to surface traces, metrics, and logs in their IDE without switching context. This high-level capability is designed to streamline debugging and reduce time spent navigating between systems, while also laying the groundwork for consistent access across AI assistants and integrations. Originally launched as an open source project, MCP is now offered by Honeycomb as a managed service.
Software development
fromPycoders
4 months agoPyCoder's Weekly | Issue #698
Move beyond chatbots to build durable MCP servers that run for days, survive failures, and orchestrate elicitations and LLM sampling. Learn remote MCP trade-offs and patterns for Anthony Shaw poses the question: Python has had async for 10 years, so why isn't it more popular? He dives deep on where async is useful and where it is limited. Associated Don't miss Glean's product launch on Sept 25th.
Python
fromTechzine Global
5 months agoLinux Foundation welcomes agentgateway project
The Linux Foundation has incorporated the open source agentgateway project into its organization. This AI-native proxy has been built from the ground up for AI environments, unlike existing solutions that have been adapted later. The project supports important protocols such as A2A and MCP. Under the wing of the Linux Foundation, agentgateway will have room for organic growth. Neutral governance prevents dependence on individual suppliers. This model has proven itself in other successful open source projects.
Artificial intelligence
fromInfoQ
5 months agoMCP C# SDK Aligns with New Protocol Specification, Bringing Security and Tooling Updates
One of the most notable updates in this version is the new authentication protocol. It as explained separates the roles of the authentication server and the resource server, making it easier to integrate with widely used standards such as OAuth 2.0 and OpenID Connect. It is stated that the goal is to improve both flexibility and security when managing access to external resources.
Artificial intelligence
fromThe Hacker News
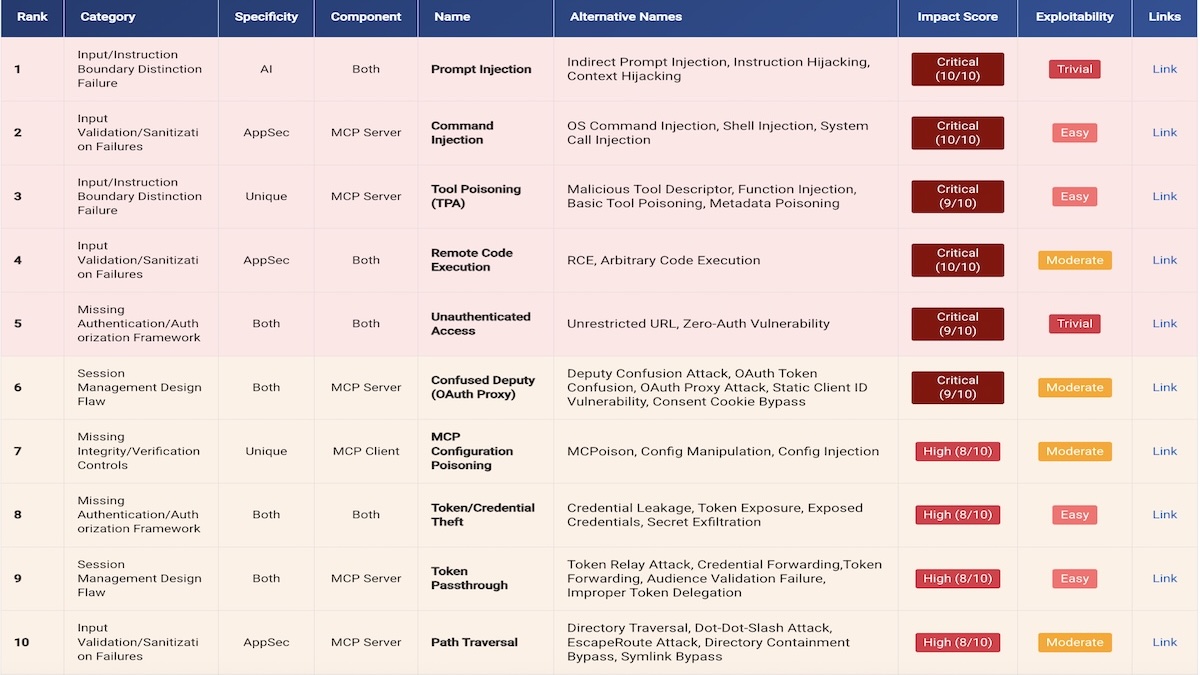
6 months agoCritical mcp-remote Vulnerability Enables Remote Code Execution, Impacting 437,000+ Downloads
The vulnerability allows attackers to trigger arbitrary OS command execution on the machine running mcp-remote when it initiates a connection to an untrusted MCP server, posing a significant risk to users - a full system compromise." Or Peles, JFrog Vulnerability Research Team Leader, said.
Information security
Online Community Development
fromAmazon Web Services
9 months agoExtend the Amazon Q Developer CLI with Model Context Protocol (MCP) for Richer Context | Amazon Web Services
Amazon Q Developer CLI now supports Model Context Protocol (MCP), enabling developers to connect to external data sources for improved context-aware AI responses.
[ Load more ]